A Simple Trick to Hack Unprotected Surveillance Cameras in Web
This is pretty much exposing post about the level of security issues in India. I’m not sure if this is practically being exploited to target broadband users in India. I’m going to show you the fun part here. Its up to the readers to act in an ethical way.
First you need the Angry IP Scanner. Download it from here http://www.angryip.org/w/Download. This is a simple tool that scans for a range of Live IP Addresses and identifies user specified open ports. So I downloaded the 32-bit Beta version. This doesn’t require any installation. Just download and run it.
When you open the tool you can see options to set IP ranges for scanning.

I’m a BSNL Dataone Broadband user and I wanted to find out the vulnerable cameras in my locality. So I start with my IP Address. Just go to Google and Search ‘My IP’. You will get your IP address. By the way I’m not stopping you from find your IP using ipconfig command like a geek. Googling is pretty simple.

I entered my IP 117.193.138.135 in the starting field and 117.193.255.255 in the finishing field. This will sure take a lot of time to scan the whole range but will increase the probability of finding more vulnerable cams.

Next is to specify a Port so that the Angry IP Scanner will ping each IP to find out if that port is open, Go to Tools > Preferences > Ports tab. In Port selection enter the port number you want to scan. I noticed that in my locality most of them are using HIK Vision Digital Video Recorder. This device uses the port 8000. So I’m entered port 8000 in the text box.

If you want to scan multiple ports you can enter port number separated by commas. After entering the port number go to Display tab. This where you can customize the results displayed. By default All Scanned Hosts will be checked. In this mode all Dead IP wil be displayed in Red, Alive in Blue and Open Ports in Green. So I recommend to select Hosts with open ports only so that you need not scroll through the entire ocean of Dead and Alive IPs. Once done click OK.

Now click on Start button and wait for sometime. If you have selected All Scanned Hosts in Display tab, you would have seen individual IP being scanned and listed.
Looks like I got three targets. Just right click on the IP Address to copy it.

Paste the link in the Address Bar of your Internet Explorer and hit Enter. Success!!! It loads the login page. As expected its the login page of HIK VISION DVR. The reason why we are using IE is that the ActiveX designed to handled these pages can work only with IE. Even in IE sometimes you will have to wait for the prompt to install ActiveX Control for HIK Vision. If your IE blocks the addon, watch this video http://youtu.be/RymqP4uDC9U to enable it. (or Google ‘enabling unsigned activex control in IE’)

Here is the trick. Most of the targets after installing their networked DVR, they fail to change their credentials from the default one provided by the manufacturer. So for HIK VISION the default username : admin and password : 12345
If you come across a different manufacturer you can just Google the name of the manufacturer with term ‘default password’ to find out the default credentials.
So I entered the default credentials and tried to login. Voila!! I’m in. It seems to be a security cam of a Fashion showroom.


You can browse through various available cams placed in different positions. The interesting part is you can even access the earlier recorded clips of these cams.
Lets go back to IP Scanner and check out if we got any more targets. To our Surprise we got a more than a dozen targets.
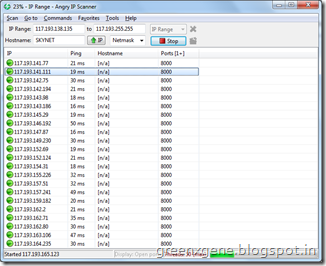
By now you would have got an idea of the extent to which our security is vulnerable. Instead of port 8000 if you scan for 80 you will get mostly online Broadband Routers around your place. Again each router manufacturer will have a default username and password. I will cover this in another post in future.
Likewise IP with open Port 3389 will allow you to make Remote Desktop Connection with them. Just repeat Step 5 with Port 3389.

IP with open Port 445 will allow you to access the shared folders.

This post is to create awareness among citizens to change their default passwords of their networked devices. I do not hold responsibility if someone misuses the process in this post.


Comments
Post a Comment